What is ransomware?
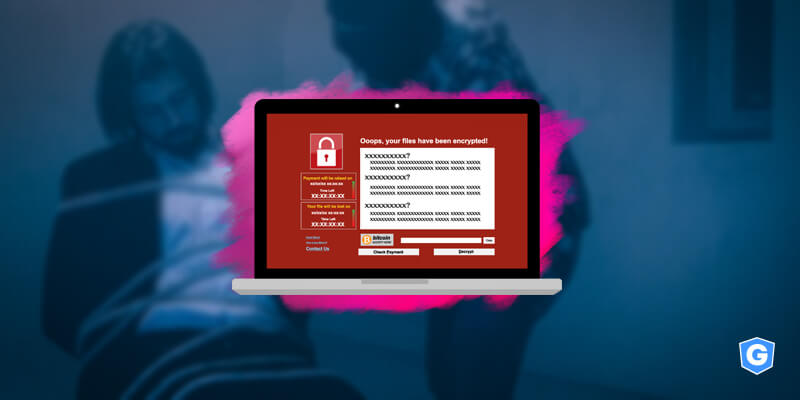
Ransomware is a malware that, after being installed, encrypts the files on your machine or blocks your system. Then, just as in a hijack, a ransom is required, hence the name ransomware, so that the files are returned or the system released.
In general, the payment is requested in cryptocurrency, such as bitcoin and monero, so that it’s impossible to be tracked, securing the hacker identity.
According to Europol’s 2020 report, the Internet Organized Crime Threat Assesment (IOCTA), ransomware remains one of the main threats in the cyber world. Ransomware has been at the top of the list since 2015.
The FBI has a similar opinion, since ransomware has a prominent place in the Internet Crime Report every year. The losses caused by this type of malware have risen sharply: from USD 8.9 million in 2019 to USD 29.1 million in 2020.
Keep reading to learn more about what ransomware is and how attacks work.
Table of Contents

How ransomware attack works
The most common vectors of ransomware are malicious emails, via phishing scams, and vulnerabilities in RDP (Remote Desktop Protocol) solutions.
In practice, ransomware operates so that, by infecting the device, it encrypts user files and apps or forbids access to the entire machine’s operating system.
When the encryption process ends, a screen appears saying the device has been infected and that a ransom needs to be paid or the files will be deleted within hours.
Due to the fact that it’s usually an advanced threat, ransomware is difficult to detect. Depending on the case, it can even fool security software.
The worst news is that we are all potential victims, as ransomware can hit Windows, Mac, Linux, iOS and Android.
What are the types of ransomware
There are 2 types of ransomware, or 2 main categories:
1. Cryptor or encryptor
Cryptor ransomware encrypts only some files and apps. That is, it still allows you to access your machine partially.
2. Blocker or locker
Locker ransomware, as the name suggests, is a more extreme type of ransomware, blocking your entire operating system.
RaaS (Ransomware as a Service)
There is still an evolution of this digital threat that has recently emerged and hugely increased its dissemination capacity: Ransomware as a Service (RaaS).
RaaS is a super profitable business. It works like this: criminals with better programming skills create ransomware to sell or rent the threat to other less qualified hackers.
As a result, hackers around the world have access to powerful weapons that make attacks more complex and scalable. Notice that, in this case, the cybercriminal doesn’t need to have advanced technical knowledge.
To set up a strategy and commit a scam, he just needs to know the ways to acquire ransomware, how to investigate profiles, how to extract data from the internet, and how to handle email tools.
RaaS has made it much easier to access threats, so much so that different agencies, such as the FBI and Europol, have already spoken out on the issue.
What is the relationship between phishing, social engineering and ransomware
Phishing
According to a Coveware’s report, about 30% of ransomware attacks involve phishing emails. That is, as you already know, phishing is one of the main vectors of ransomware.
By the way, phishing happens when the hacker fires a persuasive email in order to lure his victim into a trap.
This trap involves the use of malicious attachments and links. For example, when a user clicks on a malicious link within an email and then is redirected to a website. Then, he is induced to download ransomware without knowing it.
Social engineering
Social engineering is a technique widely used in ransomware attacks.
It happens when the criminal performs detailed and complex research on his target, which can be a person or a company. From there, he selects the victim and draws a profile with data extracted, usually, from the web.
Imagine, for example, that you received a connection invitation on Linkedin. After that, the person sends a message to you introducing himself and asking for your email.
You provide the email and then receive an attachment with an alleged partnership proposal, which is actually ransomware.
Real cases of ransomware attacks
Are you still unsure whether these attacks actually happen? Well, that’s why we have created a list with some real cases of ransomware attacks.
Ryuk
Ryuk has already caused more than USD 60 million in losses, according to the FBI. This ransomware became famous in 2018 when it hijacked data from major newspapers in the U.S. and affected more than 100 companies.
WannaCry
WannaCry is maybe the most devastating ransomware in history, launched in 2017. The damage caused by it is estimated to reach USD 4 billion.
CryptoLocker
CryptoLocker was launched in 2013. It’s a milestone for its time, infecting more than 200,000 devices and causing losses of USD 3 million.
Are you curious about other examples? Check out our list of real and famous cases of ransomware attacks.
Now, let’s go further back in time and get to know the history of the first ransomware.
History of ransomware
Did you know that the first ransomware in history was created by a biologist who studied at Harvard?
AIDS Trojan (also known as PC Cyborg) was developed by the considered father of ransomware, Joseph Popp, who distributed floppy disks infected with the malware.
The victims were participants at the World Health Organization’s international AIDS conference, in Stockholm, Sweden, in 1989.
The required amount was USD 189. The money had to be sent to a mailbox in Panama.
What to do if my business gets hit
If your company suffers a ransomware attack, would you have the proper structure to solve the problem?
The first impulse of many companies is to give in to the pressure and pay the ransom. But we don’t recommend paying for the following reasons:
- You have no guarantee that you will receive the decryption key.
- You validate the business model used by the cybercriminal.
- You’ll probably be the target of new scams from the same hacker.
- You encourage cybercrime to attack other people and companies.
In fact, this is the same opinion of international security agencies, such as the FBI.
No More Ransom
In case of infection by ransomware, one of the solutions for data recovery is to use the help of the No More Ransom (NMR) project, which provides a series of decryption keys.
Just go to nomoreransom.org to get more information.
Gatefy is a partner of NMR. We support the cause and work together to educate people and businesses, and to fight ransomware attacks.
How to protect from ransomware
Protection against ransomware doesn’t differ much from protection against most malware. We recommend:
- Keep systems up to date.
- Perform backups frequently.
- Invest in team education.
- Manage access and permissions carefully.
- Adopt security solutions, such as advanced email protection.
Remember that a ransomware attack can have different types of consequences, such as:
- Financial loss.
- Legal problems due to data protection laws.
- Data breaches.
- Theft of sensitive data.
- Blackmail (77% of ransomware attacks involve threats of leaks).
Advanced security for businesses
Now, are you interested in learning more about advanced protection solutions for your company?
Schedule a demo and get to know Gatefy products. We are experts in artificial intelligence and email protection.
If you liked this article, in which we covered what ransomware is and explained how the attack works in detail, you can not miss the news from our blog.




