Biggest hack in the history of Twitter involves social engineering: what we can learn from that
- Updated at March 19, 2021
- By Gatefy
- Blog, Security News
On Wednesday, June 15, the biggest hack in the history of Twitter took place. Accounts belonging to Bill Gates, Elon Musk, Barack Obama, Jeff Bezos, Joe Biden, Warren Buffett, and other personalities posted a similar message that promised to double the money of those who sent bitcoins to a particular wallet.
However, the reality was quite different. It was a scam, probably, involving social engineering and cryptocurrency. One of the fake tweets said:
“Everyone is asking me to give back, and now is the time. I am doubling all payments sent to my BTC address for the next 30 minutes. You send $1,000, I send you back $2,000. Only going on for 30 minutes! Enjoy!”.
The damage caused by the fraud already exceeds USD 115,000.
As soon as the threat was detected, Twitter removed the posts made by cybercriminals and locked down the affected accounts.
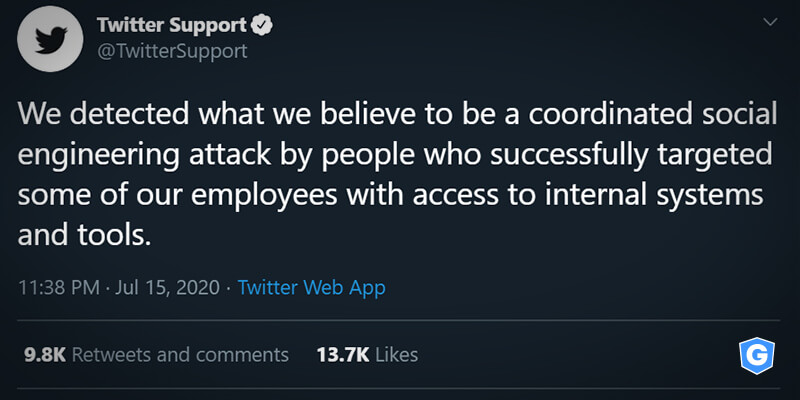
“We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools”, Twitter said.
Table of Contents

What is social engineering and what are its characteristics
Social engineering is a technique that involves persuading and manipulating the victim. The hacker studies his target carefully with the aim of getting something from him, be it money, confidential information, or access credentials, for example.
This type of attack usually happens through malicious emails, and is linked to other scams such as phishing, spoofing, and impersonation. Social engineering attacks also almost always target strategic and high-ranking people within companies.
In this case of Twitter, the targets were employees who had access to internal systems and tools.
To give you an idea, according to a Verizon’s report, social engineering attacks are related to about 22% of cases of data breaches.
So yes, social engineering is one of the techniques most used by cybercriminals and is often used as a gateway to deploy different types of malware, such as ransomware, trojans, and spyware.
What we can learn from the Twitter hack
What we can learn from Twitter intrusions is perhaps the most important question we should ask ourselves in a situation like this.
Undoubtedly, the main and first point to be analyzed in this case is about privileges. It’s clear that employees targeted by the fraud had access to a tool that allowed hackers to take over the account. In fact, all companies are subject to scams and fraud, not only Twitter or other enterprises.
But, regardless of the organization’s size, you need to have control over the information. The company needs to know exactly where the information is, who can access it, how and when.
In this sense, Twitter had a quick response to the incident. But this won’t free the company from criticism and objections.
Another key point that deserves attention when we talk about breaches and security incidents involves cybersecurity awareness or employee training.
The most lethal cyber attacks, such as BEC (Business Email Compromise) scams, for example, exploit the human factor. But what is this? The human factor is precisely your team. Is it properly trained and attentive to recognizing and fighting fraud?
Finally, what calls our attention in this case of Twitter is the sense of urgency and the promise of making money quickly and easily. These are perhaps the tactics most used in scams and frauds on the internet.
The combination of a tempting promise with a sense of urgency, after all, “you only have 30 minutes”, is explosive. To block a threat, knowing how to recognize signs of fraud is as important as using security solutions.
By the way, here at Gatefy, we offer two advanced email security solutions. They fight social engineering, phishing, BEC, and other threats.
Our solutions are compatible and easily integrated with different types of email platforms, such as Office 365, G Suite, Exchange, and Zimbra.
If you want to get to know Gatefy better, visit our solution’s pages: Gatefy Email Security and Gatefy Anti-Fraud Protection.




